Encryption, With digital technology now dominating our lives, protecting data security has become of the utmost importance. No matter whether it is personal information, financial transactions or confidential corporate records – protecting our information from hacker access has never been more urgent. Encryption plays an essential role in safeguarding this vital infrastructure; in this article we look into its background principles and contemporary applications.
1. Introduction
Encryption refers to converting plaintext (readable data) to unreadable ciphertext for security. It forms the cornerstone of modern security technologies and ensures sensitive information remains private from malicious agents who could potentially gain access.
In this article we’ll delve deep into the intricacies involved with encryption: its history and development as well as various encryption techniques currently employed today and their current applications. Furthermore, we will discuss challenges to security brought on by technological innovations as well as potential solutions to address them.
2. Acknowledging Encryption
Encryption is necessary because digital data security issues necessitate it. Without encryption, data transmitted in plaintext form leaves it susceptible to interception, eavesdropping, and unauthorised access by any means necessary. Encryption acts as an anti-hacker safeguard; even if someone manages to gain entry to your files they won’t be able to discern its contents without an access key for encryption.
Encryption becomes particularly relevant in situations like these:
Secure Communication This technology ensures instant messages, emails and various electronic forms of communications remain safe and private. Data Storage The data that’s been encrypted into servers or cloud storage platforms remains protected against unapproved access from unauthorized individuals or devices.
Electronic Commerce and Online Banking: Both provide secure financial transactions while protecting personal information when shopping online or managing accounts at banks.
Healthcare and Medical Records: Patient records that contain sensitive medical information should be protected to comply with privacy laws and protect patient confidentiality.
Government Security as Well as National Security: Encryption plays an integral part in safeguarding classified data and providing national security.
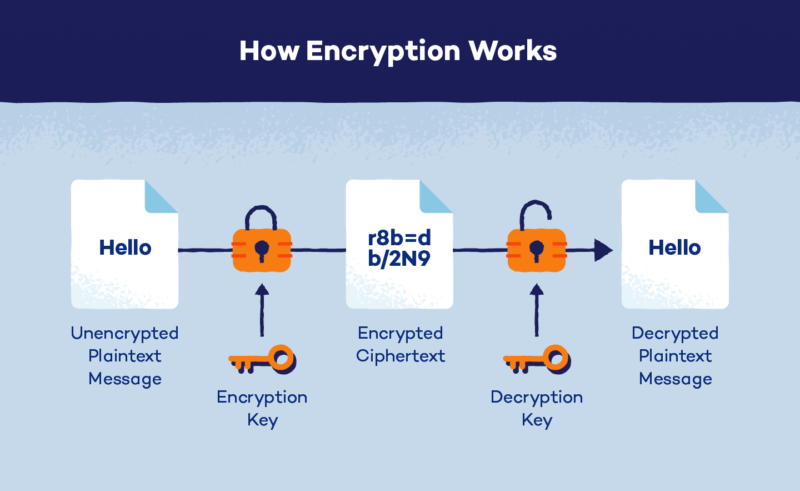
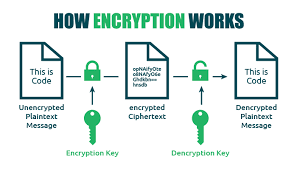
Encryption works by changing information into the unreadable form (ciphertext) using an algorithm and encryption key, only those possessing decryption keys being able to revers this process and gain access back into its original form (plaintext).
Plaintext Information that needs protecting, such as emails or documents.
Ciphertext Ciphertext, or encrypted plaintext, appears like random information and cannot be decrypted without having access to its decryption key.
Encryption Algorithm: An encryption algorithm is a mathematical procedure that transforms plaintext to encrypted text, typically through one of various techniques that each offer their own set of strengths and weaknesses.
Decryption Algorithm It works exactly the opposite way to an encryption algorithm, using both the encrypted text and decryption key in order to transform into its original form, producing plaintext in its original state.
Key for encryption: An encryption key is an integral component in the process of encryption, being an information piece used in algorithms used to convert plaintext text to encrypted data. Encryption keys provide essential protection of encrypted information.
3. History of Encryption
Encryption has an incredible and longstanding history dating back centuries.
Encryption techniques have long been in use throughout history in various forms; one such ancient form dates back to ancient civilizations. One well-known form is known as Caesar cipher which may have been utilized by Julius Caesar himself to secure key military communications; using this simple substitution cipher each letter is moved left or right by an agreed upon number of positions along alphabet.
Transposition ciphers, an ancient form of encryption, employ transposition-based cipher devices for changing letter sequences within plaintext according to certain rules or keys; one example being Scytale used by ancient Greeks; this tool employed transposition based cipher devices like Scytale.
3.2 Enigma Machine One of history’s most notorious episodes involves Nazi Germany’s use of an Enigma machine during World War II. This electromechanical device produced encrypted messages to facilitate military communications; breaking it was an enormous challenge but eventually accomplished at Bletchley Park by British cryptanalysts such as Alan Turing; this breakthrough is widely considered crucial in helping secure victory during this conflict.
Also Read: what-is-a-stakeholder-definition-types-examples
3.3 Modern Encryption
Computers brought with them remarkable technological advances for encryption technology. One widely-used encryption standard at first was Data Encryption Standard (DES), created around 1970, then later vulnerable to brute-force attacks from more powerful computers; as they evolved further this led to creation of more secure algorithms like Advanced Encryption Standard (AES).
Modern encryption techniques rely heavily on mathematical algorithms and strong encryption keys to safeguard data. Public-key cryptography, commonly referred to as Asymmetric encryption, was introduced during the 1970s and revolutionized secure communications by providing safe methods of transmitting encryption keys through unprotected channels.
4. Types of Encryption
It is possible to classify encryption into two forms – Symmetric and Asymmetric encryption.
4.1 Symmetric Encryption
With symmetric encryption, one and the same key are used for both encryption and decryption of information, while keeping their secret in order to safeguard data security. Popular examples of such algorithms are DES, AES and 3DES; though faster than their asymmetric counterparts it requires secure communication of its encryption keys among multiple parties in order to function safely.
Asymmetric Encryption
Asymmetric encryption utilizes two keys – public to encrypt, private for decrypting. Anyone has the capability of making use of public keys but only those possessing private ones can read/decrypt messages securely; this technology makes symmetric encryption unnecessary in this regard; for instance RSA and ECC (Elliptic Curve Cryptography) are two popular algorithms which employ this system of cryptography.
5. The Encryption Process
To further our understanding of encryption and decryption processes, let’s review some of the most prevalent practices involved with both processes.
5.1 Key Generation
In symmetric encryption, the first step involves creating an encryption key which must remain secret and only shared among authorized individuals. Asymmetric encryption works differently as keys are generated using two individual public and private keys combined together – where one key may be shared widely while its opposite must remain private and undeciphered by individuals.
Step 5.2.1 Secure Data With Encryption
The next step for both Asymmetric and Symmetric encryption will be securing data using encryption keys: with Symmetric it uses one single key while for Asymmetric it utilizes private keys to decrypt.
Decrypting Data
For data decryption to work properly, recipients require accessing their respective keys in order to decrypt. Symmetric encryption uses identical keys when decrypting and vice versa while Asymmetric uses private keys that may also be utilized to decrypt.
6. Contemporary Applications
Electronic circuit technology can be applied in an assortment of fields.
One of the key functions of encryption technology is protecting communications. Any time an email, phone call, or website with “https” in its URL are made or received using encryption protocols that prevents their content being seen and intercepted by malicious individuals.
Encryption is essential in protecting data that’s in storage on all of our devices and servers – whether a laptop, server or cloud storage service provider. Even if a thief gains physical access, they wouldn’t have access to your files without your encryption key.
6.3 E-commerce and Online Banking
Every time you make an online purchase or access your balance on the Internet, encrypted transactions are used to protect both financial transactions as well as personal data that could lead to identity theft.
Encryption in Healthcare and Medical Records
Encryption has an integral place in protecting medical records and patient records in healthcare, particularly with regulations like Health Insurance Portability and Accountability Act (HIPAA) mandating its usage by healthcare providers to safeguard patient privacy and ensure data security.
Also Read: Understanding Software as a Service (SaaS): Revolutionizing the Software Industry
Government and National Security
Today’s governments depend upon encryption technology to secure classified information and maintain national security. Security services, military branches and diplomatic services utilize encryption as part of their daily work practices in protecting communications as well as sensitive data.
7. Challenges and Future Trends
Encryption can be an invaluable way of protecting data; however, its implementation does not come without complications in today’s ever-evolving digital universe.
Quantum Computing Threats
Quantum computing presents an imminent danger to current encryption algorithms. Quantum computers could breach commonly utilized techniques like RSA and ECC by solving difficult mathematical issues at an unprecedented speed, potentially undermining them entirely.
Researchers are exploring post-quantum cryptography as an antidote against quantum computing’s threat; its methods aim to protect digital communications against attacks from quantum computers while guaranteeing their continuous security.
Usability and Key Management
One of the greatest difficulties related to encryption lies with user friendliness. Handling keys responsibly may prove challenging; therefore it is crucial that encryption become user friendly tools so users are taught on best practices for handling keys for secure encryption.
7.4 International Regulations
Encryption has become an important topic of international political discussions, with certain governments pushing harder for stronger encryption or backdoors that allow surveillance capabilities. Finding an acceptable balance between security and privacy remains difficult.
Conclusion
Encryption technology has long been essential to digital data security in an interconnected world, from ancient ciphers to advanced encryption algorithms and from providing us with privacy to protecting personal information and identity theft protection. While technology continues to advance and advance rapidly, encryption faces both challenges and opportunities as it advances – from quantum computing posing a danger to post-quantum cryptography emerging as a viable option; nonetheless, it remains an invaluable way of safeguarding personal information while its value will only increase further over time.